The ServiceNow GRC product contains three main applications:
- Policy and Compliance Management
- Risk Management
- Audit Management
Benefits
The GRC-related applications allow your organization to:
- Manage issues to track remediation or issue exception
- Document and publish policies
- Download and import UCF content
- Utilize controls and mitigate risk
- Assess risk exposure
- Continuously monitor risks and controls
- Plan and conduct internal audits
New version
The new Helsinki version replaces the legacy GRC application and has an improved interface and new features.
From the wiki on ServiceNow GRC:
The legacy GRC (com.snc.governance) plugin has been deprecated. Instances upgraded from a previous release can continue using legacy GRC, but the plugin is not available for activation.
Policy and Compliance Management
Policy and Compliance Management provides a centralized process for creating and managing policies, standards, and internal control procedures that are cross-mapped to external regulations and best practices. Additionally, the application provides structured workflows for the identification, assessment, and continuous monitoring of control activities.
ACTIVATE
There are four related plugins for Policy and Compliance Management:
- GRC: Policy and Compliance Management - provides a centralized process for creating and managing policies, standards, and internal control procedures that are cross-mapped to external regulations and best practices. Additionally, the application provides structured workflows for the identification, assessment, and continuous monitoring of control activities.
- GRC: Performance Analytics Premium Integration - add-on that provides GRC: Policy and Compliance Management with the capability to download regulatory content and common controls from the Unified Compliance Framework (UCF).
- GRC: Compliance UCF - add-on that provides GRC: Policy and Compliance Management with the capability to download regulatory content and common controls from the Unified Compliance Framework (UCF).
- GRC: Workbench - gives GRC administrators a graphical interface to create profile and risk dependencies. These relationships enable consistent risk mapping and modeling across the enterprise.
HOW IT WORKS
1. Dependency modeling and mapping
Dependency modeling is one of the activities required in order to ensure that an organization establishes a uniform definition of risk across the enterprise. The dependency model defines what relationships are allowed between different types of areas in the organization. This enables more effective risk normalization and aggregation by allowing stakeholders to more effectively compare and contrast risk appetite and exposure at various levels of the enterprise.
2. Compliance
Reports and Dashboards
Seven reports included. They also include three dashboards.
Compliance Overview
Policy Overview
Example Report
Control
Authority Documents
Authority documents define policies, risks, controls, audits, and other processes to ensure adherence to the authoritative content.
Each authority document is defined in a record and the related lists on that record contain the individual conditions of the authority document.
The relationships of these authority document related list items are visible in the GRC Workbench in the Policy and Compliance Management application.
Authority Document
Citations
Citations contain the provisions of the authority document, which can be interrelated. Citations break down an authority document into manageable themes.
You can create citations or import them from UCF authority documents and then create any necessary relationships between the citations.
Citation
3. Policies and procedures
Provides an executive view into compliance requirements, overall compliance, and compliance breakdowns so areas of concern can be identified quickly.
4. GRC profile scoping
The Scoping module contains profiles and profile types for use in all GRC-related applications. They can be created for any record on any table.
5. Controls
Controls are specific implementations of a policy statement. Retired controls do not appear in the list.
Controls inherit the Type, Category, and Classification from the policy statement. Controls are generated from the profile types that are assigned to a policy statement.
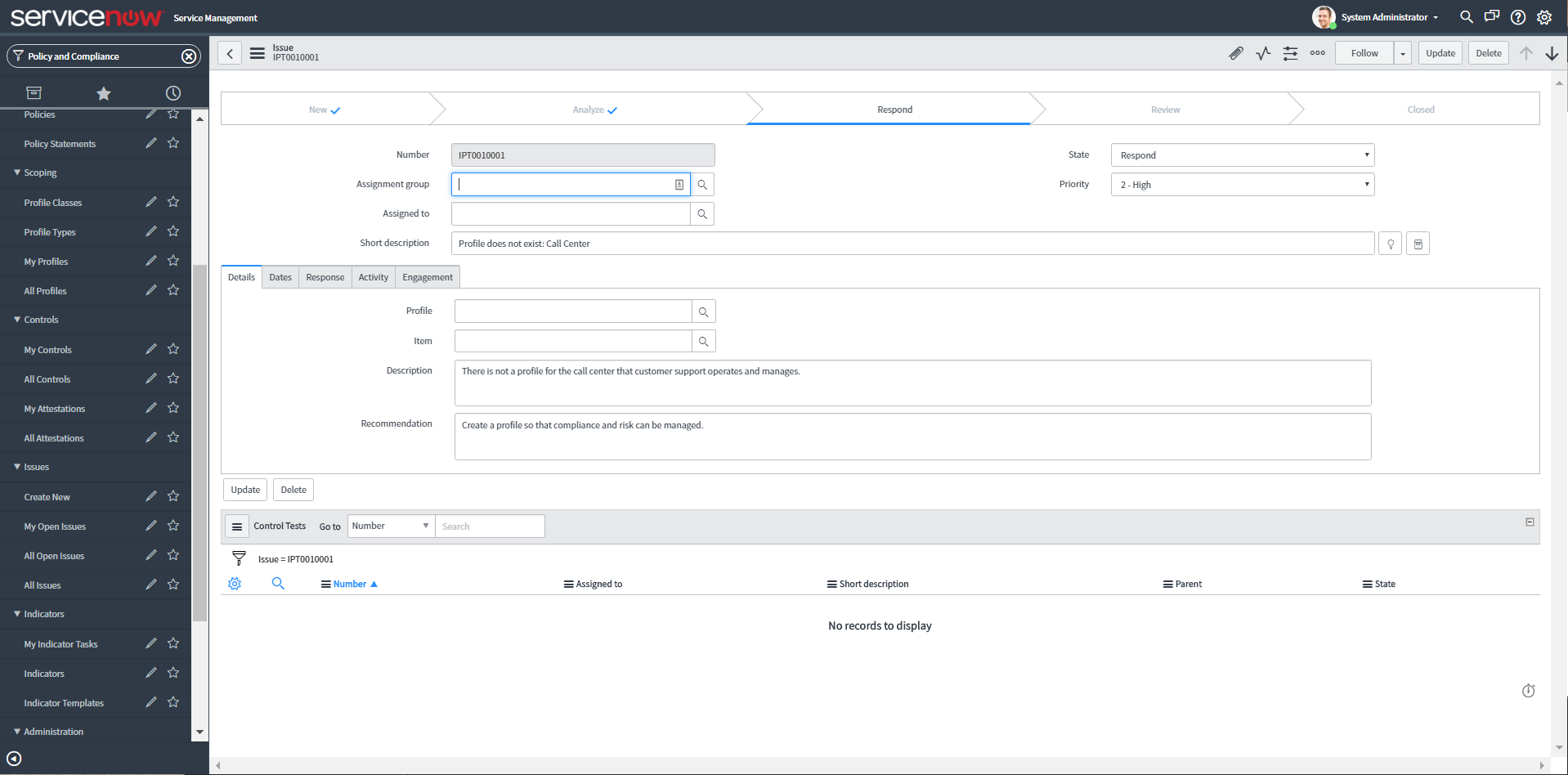
6. GRC issues management
Issues can be created manually to document audit observations, remediations, or to accept any problems. They are automatically generated from indicator results, attestation results, or control test effectiveness.
An issue is created automatically when:
Issue
- Issue - An indicator fails
- Control issue - A control attestation is completed indicating that the control is Not implemented
- Control test issue - A control test is closed complete with the control effectiveness set to Ineffective
- Other issue - is created by the user manually
Remediating an issue marks an intention to fix the underlying issue causing the control failure or risk exposure. Accepting an issue marks an intention to create an exception for a known control failure or risk. Controls that are Accepted remain in a non-compliant state until the control is reassessed. In this way, the issue can be used to document observations during audits.
7. GRC continuous monitoring
Continuous monitoring involves activities related to identifying and creating key risk and controls indicators. Supporting information can be collected for those indicators through automatic data collection or manual tasks. Indicator results are then used to create issues for controls, update risk scores, and provide supporting information for audit activities and control testing.
This uses PA.
8. GRC PA Indicators
GRC PA Indicators link GRC content and items to Performance Analytics indicators, breakdowns and thresholds. You can associate Performance Analytics indicators with risk statements, risks, policy statements, and controls to view scorecards and trends and analyze current conditions and trends.
The risks and controls associated with a PA indicator or PA indicator/breakdown/element automatically monitor any PA threshold with the same PA indicator or PA indicator, breakdown, or element relationship. Any PA threshold breach is reported at the risk or control and Performance Analytics indicators relationship level within a breach counter.
This uses PA.
9. Policy and Compliance Administration
The Policy and Compliance Management application provides properties associated with article templates, attestation types, and UCF integration.
MORE INFORMATION
For the full documentation on this application, check out the wiki:
Risk Management
Risk Management provides a centralized process for Internal Audit teams to automate the complete audit lifecycle. Project driven audits allow auditors to quickly scope engagements, conduct fieldwork, collect control evidence, and track audit observations.
ACTIVATE
There are two related plugins for Policy and Compliance Management:
- GRC: Risk Management - centralized process to identify, assess, respond to, and continuously monitor Enterprise and IT risks that may negatively impact business operations. The application also provides structured workflows for the management of risk assessments, risk indicators, and risk issues.
- GRC: Workbench - gives GRC administrators a graphical interface to create profile and risk dependencies. These relationships enable consistent risk mapping and modeling across the enterprise.
HOW IT WORKS
1. Risk Management process
The Risk Management application provides a centralized process to identify, assess, respond to, and continuously monitor Enterprise and IT risks that may negatively impact business operations. The application also provides structured workflows for the management of risk assessments, risk indicators, and risk issues.
The Risk Managementapplication follows a standard process:
- Ensure that the settings for risk criteria and properties are correct based on the needs of your organization. Modify if necessary.
- Create profile types to group common profiles with similar risks together for easier assessment.
- Create risk statements to define a set of potential risks that could occur across the organization.
- Assign risk statements to profile types, to generate risks from statements, or generate risks manually.
- Determine the appropriate risk response (for example, Accept, Avoid, Mitigate, or Transfer), and document the justification for the response.
- Assign and complete Remediation Tasks to ensure that risk mitigation efforts are implemented.
- Utilize the Governance, Risk, and Compliance (GRC) application to track risk mitigation efforts by relating a risk to controls or policies which mitigate the risk.
2. Risk Overview
The Risk Overview is contained in the Risk Management application and provides an executive view, allowing risk managers to quickly identify areas of concern by pinpointing profiles with known high risk.
Risk
Risk Statement
3. GRC Workbench
The GRC Workbench gives GRC administrators a graphical interface to create profile and risk dependencies. These relationships enable consistent risk mapping and modeling across the enterprise.
GRC Workbench
4. Risk Library
The risk library contains all risk frameworks and risk statements. Risk frameworks are used to group risk statements into manageable categories, while risk statements group the individual risks.
5. GRC profile scoping
The Scoping module contains profiles and profile types for use in all GRC-related applications. They can be created for any record on any table.
The GRC: Profile plugin contains the Scoping module and is not visible to customers and requires activation of the Policy and Compliance Management plugin, the Risk Management plugin, or the Audit Management plugin.
Only one profile can exist for a record. That profile, however, can belong to many profile types. Profile types and profiles are used differently depending on the application:
- Risk managers use profile types and profiles to monitor risk exposure and perform risk assessments.
- Policy and compliance managers use profile types and profiles to create a system of internal controls and monitor compliance.
6. Risk Register
The risk register is the central repository for all potential risks that could occur at anytime, anywhere in the organization.
Risks are generated from risk frameworks, risk statements, and profiles, or they are created manually.
7. GRC issues management
Issues can be created manually to document audit observations, remediations, or to accept any problems. They are automatically generated from indicator results, attestation results, or control test effectiveness.
An issue is created automatically when:
- Issue - An indicator fails
- Control issue - A control attestation is completed indicating that the control is Not implemented
- Control test issue - A control test is closed complete with the control effectiveness set to Ineffective
- Other issue - is created by the user manually
Issue
Remediating an issue marks an intention to fix the underlying issue causing the control failure or risk exposure. Accepting an issue marks an intention to create an exception for a known control failure or risk. Controls that are Accepted remain in a non-compliant state until the control is reassessed. In this way, the issue can be used to document observations during audits.
8. GRC continuous monitoring
Continuous monitoring involves activities related to identifying and creating key risk and controls indicators. Supporting information can be collected for those indicators through automatic data collection or manual tasks. Indicator results are then used to create issues for controls, update risk scores, and provide supporting information for audit activities and control testing.
This uses PA.
9. GRC PA Indicators
GRC PA Indicators link GRC content and items to Performance Analytics indicators, breakdowns and thresholds. You can associate Performance Analytics indicators with risk statements, risks, policy statements, and controls to view scorecards and trends and analyze current conditions and trends.
The risks and controls associated with a PA indicator or PA indicator/breakdown/element automatically monitor any PA threshold with the same PA indicator or PA indicator, breakdown, or element relationship. Any PA threshold breach is reported at the risk or control and Performance Analytics indicators relationship level within a breach counter.
This uses PA.
10. Risk Management Administration
The Risk Management application provides properties associated with significance, likelihood, and application.
MORE INFORMATION
For the full documentation on this application, check out the wiki:
Audit Management
Audit Management provides a centralized process for Internal Audit teams to automate the complete audit lifecycle. Project driven audits allow auditors to quickly scope engagements, conduct fieldwork, collect control evidence, and track audit observations.
ACTIVATE
There are two related plugins for Policy and Compliance Management:
- GRC: Audit Management - provides a centralized process for Internal Audit teams to automate the complete audit lifecycle. Project driven audits allow auditors to quickly scope engagements, conduct fieldwork, collect control evidence, and track audit observations.
- GRC: Workbench - gives GRC administrators a graphical interface to create profile and risk dependencies. These relationships enable consistent risk mapping and modeling across the enterprise.
HOW IT WORKS
1. Engagement Overview
The Engagement Overview is contained in the Audit Management application and provides an executive view into audit results, engagement breakdowns by task, and allows areas of concern to be identified quickly.
The Engagement Overview module displays audit information that is tailored to the role of the user.
Engagement Overview
2. Engagement Workbench
The Engagement Workbench provides a timeline view from which you can select an audit engagement to view details or create a new engagement.
Engagement Workbench
3. Engagements
The audit engagement process involves creating, planning, scoping, and conducting engagements as well as reporting on engagement findings.
Engagement
4. GRC profile scoping
The Scoping module contains profiles and profile types for use in all GRC-related applications. They can be created for any record on any table.
The GRC: Profile plugin contains the Scoping module and is not visible to customers and requires activation of the Policy and Compliance Management plugin, the Risk Management plugin, or the Audit Management plugin.
Only one profile can exist for a record. That profile, however, can belong to many profile types. Profile types and profiles are used differently depending on the application:
- Risk managers use profile types and profiles to monitor risk exposure and perform risk assessments.
- Policy and compliance managers use profile types and profiles to create a system of internal controls and monitor compliance.
5. Audit tasks
Audit tasks are completed throughout an engagement and provide documented evidence that the organization is complying with external regulations and internal policies.
When audit tasks are created or reassigned, a notification is sent to the assigned user. A notification is also sent when the task reaches 75% of its planned duration.
6. Audit testing
An audit engagement may include control testing activities during which controls are evaluated for design and operational effectiveness.
7. GRC continuous monitoring
Continuous monitoring involves activities related to identifying and creating key risk and controls indicators. Supporting information can be collected for those indicators through automatic data collection or manual tasks. Indicator results are then used to create issues for controls, update risk scores, and provide supporting information for audit activities and control testing.
This uses PA.
8. GRC issues management
Issues can be created manually to document audit observations, remediations, or to accept any problems. They are automatically generated from indicator results, attestation results, or control test effectiveness.
An issue is created automatically when:
- Issue - An indicator fails
- Control issue - A control attestation is completed indicating that the control is Not implemented
- Control test issue - A control test is closed complete with the control effectiveness set to Ineffective
- Other issue - is created by the user manually
Issue
9. Audit Management Administration
The Audit Management application provides properties associated with significance, likelihood, and application.
MORE INFORMATION
For the full documentation on this application, check out the wiki: